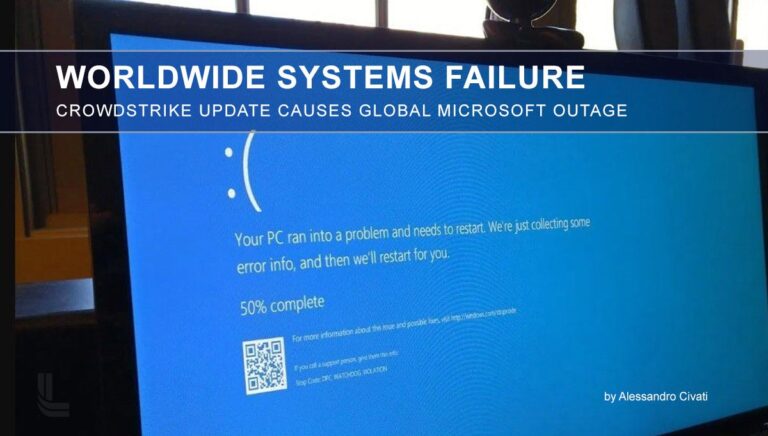
Benefits of Digital Copyright with Blockchain Technology
Copyright protection has become a complex issue in the digital age, where works can be easily copied and distributed without authorization. Challenges include monitoring the use of works, preventing plagiarism,…