About us
Our mission is to protect everyone’s ideas and let develop a safe society based on meritocracy and honesty
humanity and technology together
Our mission
A trusted web
LutinX has developed a cross-chain system where users are in control.
We are the virtual place at the base of the new web 5.0, where data is certain and provenance is certain, where those who certify and those who make declarations must be well identified (on our platform) to protect our ecosystem.
LutinX facilitates an Internet where independent blockchains can reliably exchange information and transactions through their infrastructure.
We make it easier than ever to create and connect decentralized applications, services, and institutions. We empower innovators to create better solutions, we seek to free society from its dependence on an “insecure” web.
Our goal is to become a world leader in Blockchain for education and the protection of intellectual property and copyright. We believe that lifelong learning, in any form, should be encouraged, celebrated, and accepted, as a means to improve the lives of each of us.
The problems we solve
In today’s digital world, the ability to forge, delete, or otherwise manipulate data is omnipresent. Organizations and individuals spend resources to protect and prove the integrity of their data to 3rd parties.
And what about skills and meritocracy? We help everyone track and manage their own expertise and personal & professional goals easily and intuitively. Certification, training capabilities, and more can be managed with Blockchain technology in a single place. Creating an accurate Resume now is possible with immutable data.
And we do more, like helping people and companies confirm their supply chains (not only for the food industry), and protect their intellectual property and the data they manage.
our goal is to become the leader in
Intellectual property, skills registrations, and Data Certification.
WE REINVENTED
THE INNER CONCEPT OF TRUST.
Our Eco-System is Secure & Transparent, based on the best use-case technological solution.
Usable
3 minutes to activate your full KYC account, is the time need to access the full potential of our Platform.
Multiple Apps
LutinX integrates into the main code multiple blockchain & AI applications immediately available to every user.
Legal Value
Time Stamp functionality is integrated, and you can certify every activity inside the LutinX Platform.
Scalable
Thanks to our APIs, third systems can expand the users’ trust experience worldwide in an IN/OUT direction.
Flexible
A Clear Budget
Our technology lets you know precisely how much you’ll pay for the services. We are not linked to any cryptocurrency.
with A collection of advantages
for an everyday-use
- Privacy: LutinX does not require access to underlying data.
- Security: Data is not shared among network nodes – for our services.
- Compatibility: We are working to set up a real cross-chain platform for the best worldwide interactions.
- Scalability: Designed for enterprise data volumes.
- Reporting: Dynamic reporting of multiple Blockchain proofs.
- Forensics: Data tied to the source. Creator + Data + Time.
- Trust: Trust in LutinX is not required, our proof is mathematical.
- Regulatory: Extends to regulatory use cases.
- Flexibility: Extends to any data format and file size.
- Stateless Approach: Nodes do not require complete data history of other nodes.
- Easy integration: Via open standards API, shared by us.
- Crooss-Tecnology: We jump between blockchain technologies, like Ethereum, Takamaka, Algorand, EOS, and others.
Blockchain data certification
We leverage blockchain technology to ensure the existence, integrity, and attribution of communications, processes, and data important for your organization. With LutinX it is possible to certify and authenticate any kind of data without relying on trusted third parties
Proof of Ownership
Attribution and audit trails that can be independently verified
Proof of Existence
Certify that a file, dataset, or communication existed at a certain point in time
Proof of Integrity
Monitor your data in real-time to ensure it has not been tampered with
Proof of Receipt
Certify that a specific recipient read your email at a certain point in time
Five great example of BAAS
LutinX offers multiple Blockchain As A Service solutions, like:
Data integrity: a change of paradigm
Data integrity monitoring tools such as Lutinx.com API are defining a completely new approach to system security. Instead of sitting out of monitored systems and trying to block attacks, these tools reside within them and are able to monitor, report and respond to every change that happens to critical files and registries. This is a huge paradigm shift: now you can prevent, detect and act on any kind of attack on your systems, coming from the outside or from within your organization.Lutinx.com is a Public explorer where it is possible to verify Intellectual Property Records, Skills Certifications, and membership status, Worldwide.
It is a free-of-charge solution available worldwide and accessible to anyone. But, we are not Google! With us, you can search for
- Download the Paternity Certificates of Music, Art, Legal Statements, Research, Scientific Articles, Business Research, and more.
- Verify the Common License assigned to a creation from its owner.
- Verify the Skills issued to a specific man or woman, validating the issued too.
- Verify if people or companies belong to some specific organizations.
- Verify if a membership is still active or not.
- Verify if someone went to a school or university.
- Create a FREE account and Protect your Intellectual Property Directly, without costs or timelapse.
- And, much more!
Demonable document management
Integrate the document management solution with the Lutinx.com API and take advantage of the unique power of blockchain technology.
- Create tamper-proof records of the existence and integrity of your organization’s documents, files and business processes.
- Protect the paternity and ownership of your creations and IP.
- Verify the authenticity of signed documents and communications.
- Generate immutable control tracks that keep track of all the changes that occur in a document.
Build the Internet of reliable things
In a world where the number of connected devices is growing so fast, maintaining their security and protecting us from attack is a big challenge. LutinX blockchains provide an immutable and decentralized ledger where data sets from such devices can be anchored to authenticate their legitimacy. With the Lutinx.com, the same IoT devices can even certify their own firmware and then prove their integrity to their peers, thus avoiding node hijacking or representation within mesh networks.
Critical infrastructure is now the land of blockchain
The unparalleled level of security and security offered by public blockchains is perfect for critical infrastructures and other scenarios where there is a lot at stake. In the last decades, with the obsolete transformation of the old Scada systems, Information Technology systems and protocols have gained ground for operational technology, introducing huge challenges in their security. With this in mind, the LutinX industrial certification process has been designed with the same availability, integrity, and confidentiality priorities common to all critical infrastructure systems.
The history of a product, registered forever
Materials, raw materials and products have a history behind them, and those stories are sometimes of fundamental importance for their market value. Eco-friendly soy beans, diamonds, pieces of art. You will now be able to demonstrate their origin and integrity at every stage of the supply chain without any possibility of tampering. Lutinx.com allows you to adopt the exceptional characteristics of traceability, transparency and certainty that characterize our blockchain infrastructure and to apply them to demonstrate the provenance and ensure quality like never before.
SOME REASONS TO USE LUTINX.COM
Total Accountability
For the first time in human history, an immutable layer of transparency removes friction from your auditing process.
Ultimate Security
No more need for trust in insiders or third parties. We replace trust with mathematical proof and with a biometric ID process (if necessary).
Strong Attribution
Track any action to its source, securely and transparently, in a way that can be seamlessly and independently audited.
Better Digital Evidence
Blockchain-based hashing and time stamping make for exceedingly strong evidence of the authenticity of a document.
Forensic Auditability
All evidence and audit trails generated by lutinx.com are 100% counterfeit-proof and verifiable by independent third parties.
Infinite scalability
Thanks to our technology, we can stamp up to exabytes of data and embed it on our blockchain. We also have multiple public APIs.
we offer you more
LutinX is growing every day thanks to the contribution of our fantastic team, our Partners, Ambassadors, Customers, Friends, and Users.
Insider Threat Mitigation
In normal systems, services are used to collaborate or integrate externally more and more different networks, which do not allow companies to fully control the data, thus increasing the risk of threats, especially internal ones. Systems are increasingly exposed to the fact that even internal technicians can tamper with the information present in the systems.
At Lutinx.com we mitigate this risk with our proprietary technology.
The database we use is protected by a constantly growing network of computers, distributed throughout the world (to date in over 10 countries). Each computer uses its computing power to make the register immutable and secure. We use cryptographic algorithms to record the unique identifier of each piece of information, including the identity of the person who created it. If this information is tampered with, even as a result of human “errors”, it can be quickly re-established in its previous states.
Critical Infrastructure Protection
Critical infrastructure protection is becoming necessary as even more digital threats endanger companies every day.
There is no single software stack that is safe from data tampering.
We can track the state of entire filesystems, servers, or networks, so you always know if an attacker gets in, and you can take the necessary preventive measures to minimize damage or to safeguard the penetrated systems.
... and immutable audit trails
Infinitely scalable
Bundling transactions makes it possible for us to overcome the limits of public blockchain technology. Furthermore, thanks to the cryptographic structures we use, all the stamped data can be individually and indepentendly verified.
Privacy respectful
We never publish raw data or plain text to our blockchain: We use unique cryptographic identifiers (hashes) in order not to reveal the original data. Since hashes are one-way cryptographic algorithms, you can still prove that a determinate hash relates to your data, but nobody will ever be able to obtain your data by only having its hash.
Independently verifiable
Since we use public blockchains accessible by anyone in the world at zero cost, everything is transparent and extremely easy to verify while maintaining absolute privacy. The cryptographic proofs that we generate are everything you or anyone needs to prove or verify that a given dataset existed at a certain point in time.
Machine friendly
Trust is a human creation. Machines don’t know about trust. With LutinX Blockchain, the verification of cryptographic proofs can be done automatically, enabling secure machine-to-machine (M2M) transactions in a world in which the Internet of Things is already a thing.
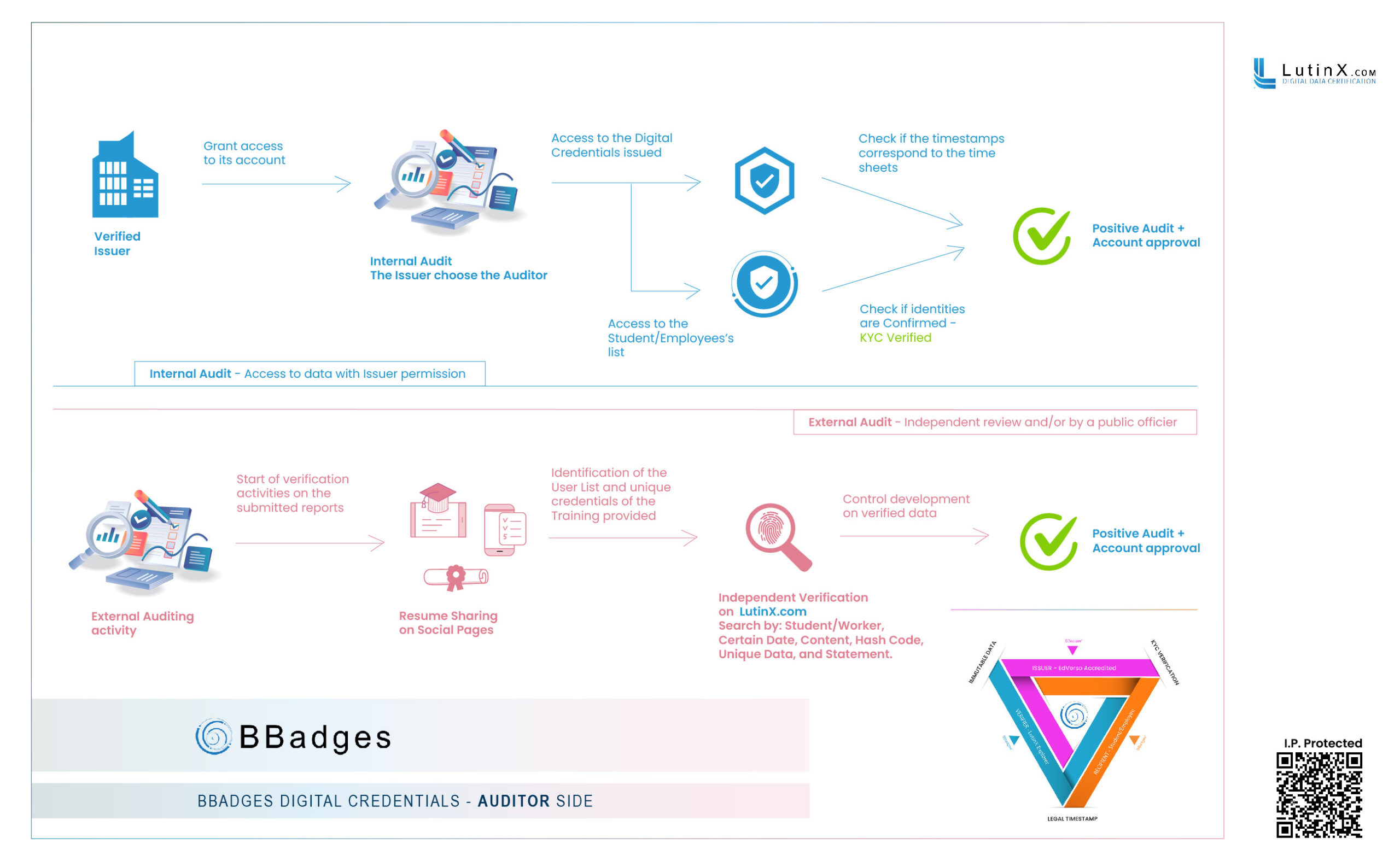
Finally, we present here an illustrative map of our Audit capabilities (currently at two levels).