Applications and Services.

support/ get an authorship certificate
We make it simple!
🎯 We used our experience to offer you a very very easy solutions. Just three steps!



HOW IT WORKS
We are proud to present our guide to using LutinX IP in less than 3 minutes.
The Steps:
- Home Page
- Login Page
- Choose the type of user
- Activate your Account
- The first login
- Let´s Start
- 👉 Protect your work
- 👉 Fill Data
And know more about:
LET´S PROTECT YOUR WORK
From now, every time you’ll Press “PROTECT YOUR WORK” in the top-right corner of our platform you’ll arrive here.
👉 7 – Choose the File Type, and Upload it.
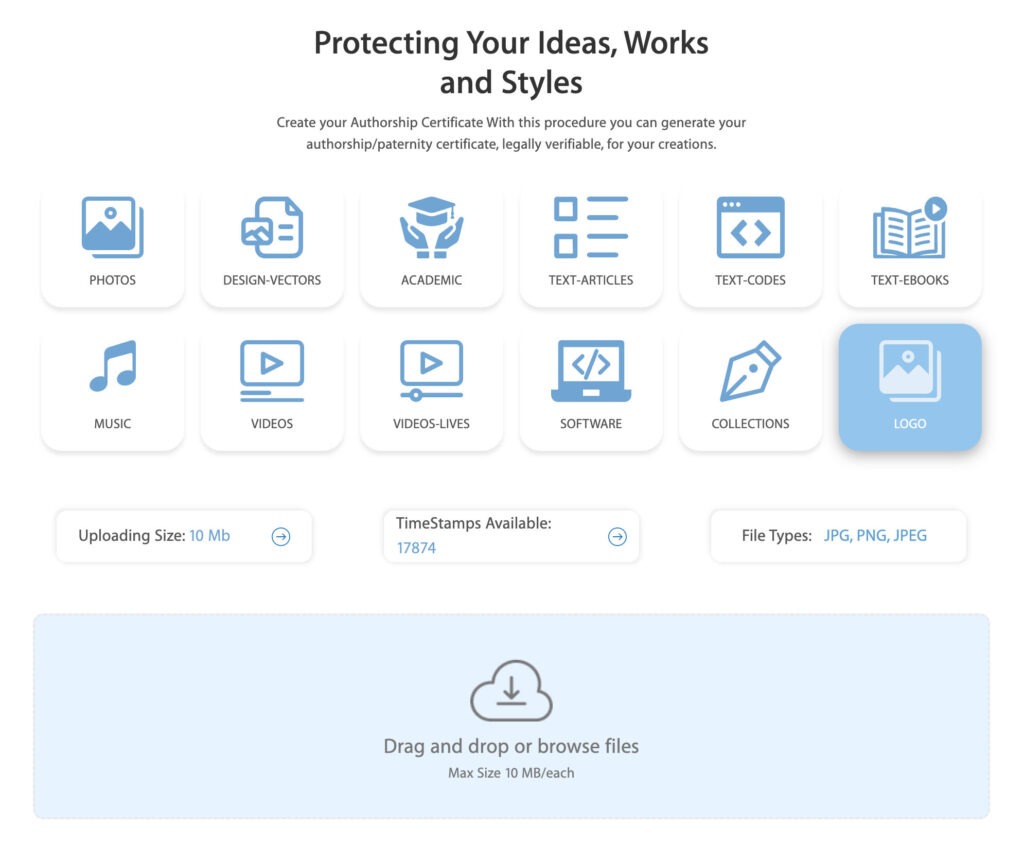
PAY ATTENTION. Before the Blue Box, you can see the “Uploading Size” Allowed, and the “TimeStamps Available” (33 initially or 100 if you completed the KYC Process).
If you want to increase the size of your uploading file or buy more Blockchain transactions you can simply press the “arrow” icon, near them.
👉 8 – Assign the Paternity References
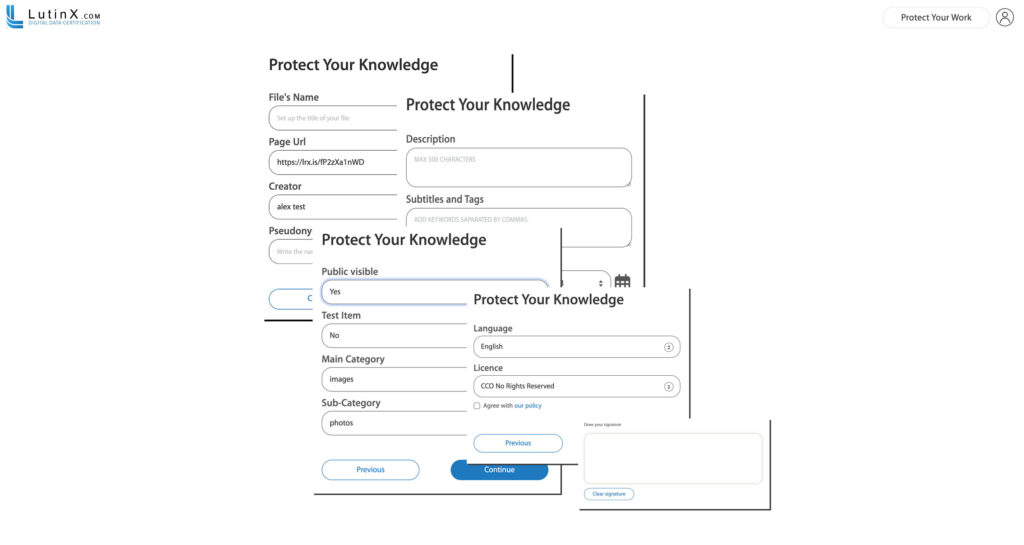
You have to fill in five simple steps, confirming
- your data,
- work references, including a public description, tags, and the creation date – It can be different from the signature process you are going to apply now;
- the modality of publication (you can choose Public NO to do not let third people reach it on our public explorer – or choose “Test YES” to set up an auto-deletion of your record in 60 days);
- select the main language of your Protected Work, and the kind of Licence you want to apply on it (you can change it anytime);
- Verify all the steps and SIGN it, directly by hand.
DONE !
From now you can access your uploaded works every time from your account (press the circle-icon in the top right corner) or directly in the public LutinX Explorer from our homepage.
KNOW MORE
Access the full potential of Blockchain for Intellectual Property by LutinX.com.
Here we provide you with the main pieces of information to work with us, without doubts.
If you need more clarifications fill free to contact us, directly from the Support Zone, inside your account.
👉 9 – LutinX IP Paternity Certificates
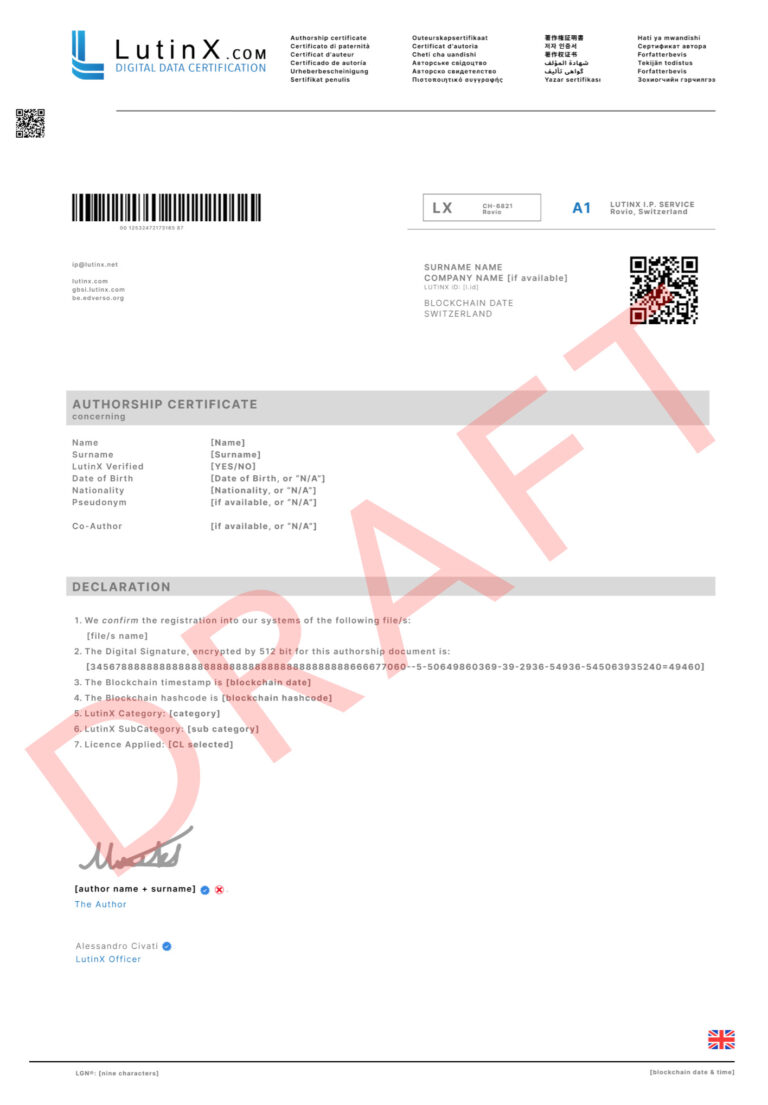
The LutinX registration protocol will chain together all certificates related to the same project, therefore allowing users to create a digital trail of records proving the evolution of the project.
Each certificate can be independently verified by any third party without any involvement of LutinX, thanks to our advanced technology.
For each document, you can create multiple reviews of it and at the same time, new certificates will be generated inside the blockchain network.
By default, all the “Archived Review” will be accessible only from the owner, that can share them with Partners, Clients, or third users.
Every Blockchain Certificate generated inside the LutinX Platform will contain strategic and unique data, visible to everyone who will get a Certificate, and Back-End Encryption Data, preserving the Data Supply Chain. This final aspect is integrated by default inside every LutinX IP Certificate.
👉 10 – Encryption & confidentiality

LutinX offers trust security levels, growing day-by-day, due to our professionals with more than 20 years of experience in Cryptographic and CyberSercurity.
Every File (docx, pdf, bmp, jpg, mp3, mp4, mov, dxs, txt, zip, rar…) is always encrypted and no one, including the LutinX Administrators, can access them. We currently offer 512bit native encryption, and from 2024 will upgrade it to 2048bit. Only the owner can share it with one or more people, directly from his/her panel.
In the last year, we invest great financial resources in Hardware Infrastructures allowing high-performance levels with multiple processor activities, working on Parallel and Cloud interfaces.
To increase the level of security and confidentiality, from every file, we extract its digital signature that we tokenize it inside specific blockchain hashes. In this way, we still respect Public Administration requirements about Data Conservatory, offering legal value to every Document archived and Protected in our Network.
LutinX offers Public Administration (Governments) his level of Security Solution in Storage Conservatory, allowing them to respect their Digital Regulations and Bring instantly to the Web3 world, ready to access new levels of data development with Artificial Intelligence and Big Data Analysis.

