The history of cybersecurity regulation can be traced back to the 1990s when the E.U. passed the Data Protection Regulation. Shortly after, the U.S. established a President’s Commission on Critical Infrastructure Protection to identify and protect critical infrastructure, culminating in the National Strategy to Secure Cyberspace in 2001; now, the U.S. took global cybersecurity leadership. Ever since the U.S. Congress and States have passed numerous laws and regulations in the cybersecurity space. The U.S. Department of Homeland Security (D.H.S.) created the U.S. Computer Emergency Response Team (US-CERT) to facilitate public-private sector information sharing on cyber threats. The U.S. Cyber Command was established in 2008 by the Secretary of Defense to protect U.S. national security interests.
The European Union has recently passed the Global Data Protection Regulation (GDPR) in 2018 to add another layer of regulations to fight increasing cybersecurity incidents and protect critical infrastructure. The E.U. has some of the most rigid data protection laws in the world. The passing of the GDPR had far-reaching ramifications for businesses worldwide that are faced with fines of up to 2-4% of their total global turnover if found guilty. From 2013 when the E.U. Cybersecurity Strategy was passed, the E.U. has aggressively passed and enacted cybersecurity laws, particularly in data privacy, that most U.S. businesses haven’t paid attention to.
Most businesses, especially those in the U.S., are unaware of E.U.’s cybersecurity regulatory frameworks, especially the Directive on Security of Network and Information Systems, popularly known as the N.I.S. directive. The N.I.S. directive that came into effect in 2016 empowers E.U. member states to regulate and enforce cybersecurity requirements within their boundaries. The passing of the Communication from the Commission to the European Parliament and the Council has an annex and is meant to help member states implement the N.I.S. Directive. The Directive applies to operators of essential services (O.E.S.) that happen to be critical infrastructure companies and digital service providers.
O.E.S. companies are required to meet the following in the Directive:
- Implement all the technical and organizational security measures to prevent risks and manage the security of networks and information systems.
- Notify relevant national authorities about any severe cybersecurity incidents.
On the other hand, the Directive has imposed several obligations on E.U. member states, including:
- The development of a cybersecurity strategy.
- Establishment of a national point of contact for purposes of coordination with other member states.
- Establish Computer Security Incident Response Teams (CSIRTs) that help monitor events at the national level to provide early warnings and alerts about incidents, respond to incidents, and share information among stakeholders.
- Assign the role of checking compliance to competent national authorities. The authorities will also regularly check that O.E.S. companies are managing cybersecurity risks to their systems and networks. E.U. member states are allowed to set stricter requirements than those already established by the E.U.
- Ensure that O.E.S. companies minimize the impact of incidents and notify national authorities or the CSIRT without delay.
- Ensure that competent national authorities have the power and resources to:
- Assess if O.E.S. companies are complying with the N.I.S. Directive
- Compel O.E.S. companies to provide critical information required for assessment as well as evidence of implementation.
- Issue binding instructions to the O.E.S. company to help fic deficiencies.
The N.I.S. directive applies to U.S. companies that have operations in E.U. member states. That means that U.S. companies have to implement and comply with the security requirements captured in the regulations, hand over operational data to national authorities for compliance assessment, and provide remediation efforts. Failure to abide by the rules will attract fines and penalties set by the member states. Member states’ varying levels of enforcement of the N.I.S. directive make it difficult for U.S. companies to comply.
On the other side of the world, the U.S. Congress has passed the Clarifying Lawful Overseas Use of Data Act (CLOUD Act) that gives law enforcement authorities the right to obtain personal data from IT companies even when it’s located in data servers in other countries. Other regulations and laws are in the pipeline, and their enactment may spell another wave of changes for the cybersecurity sector.
Notable Differences in E.U. and U.S. Cybersecurity Strategies
In a brief summary, the cybersecurity strategies in the E.U. and the U.S. focus on:
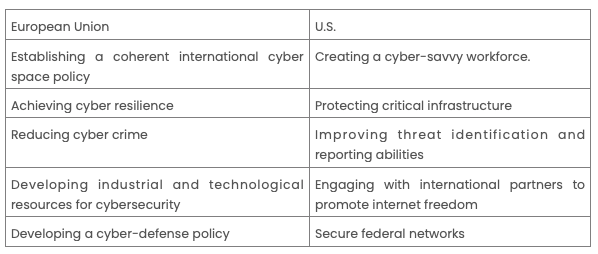
The E.U. and the U.S. do not have shared pieces of legislation in standards and certification. Each jurisdiction has identified different policy areas and developed approaches that suitably meet their unique needs. In the U.S.A., the focus for cybersecurity standards has been on the NIST Framework, a set of voluntary standards issued in 2014 and meant to improve critical infrastructure security. In the E.U., the European Commission focuses on cohesive cybersecurity laws and therefore developed the N.I.S. Directive. The Directive requires all E.U. member states to keep to the set of standards and always be adequately prepared before, during, and after a cybersecurity breach.
Despite the divergent approaches to cybersecurity laws and regulations, one area of consensus has been the importance of public-private information sharing. There’s the recognition of the role of that information sharing in preventing and mitigating attacks, especially of digital service providers (D.S.P.) and operators of essential services (O.E.S.s). The GDPR and the N.I.S. directive have made it mandatory for data controllers and data processors. It also mandates that O.E.S.s report cybersecurity breaches to data protection authorities immediately. In the U.S., the Cybersecurity Information Sharing Act (CISA) facilitates companies to monitor cybersecurity threats, implement defensive measures, and share information with other companies and the federal government.
In conclusion, policy discussion between the E.U. and the U.S.A. will set the stage for strong cooperation, especially about emerging cybersecurity trends and protecting an open and interoperable Internet.

Author: Alessandro Civati
Blockchain ID: https://x88.life/GZE2R9zTQm






